Table of contents
- Introduction
- The Customer Service Fraud Paradox
- The Anatomy of Customer Service Fraud
- How Fraud Detection Works in Customer Service
- Machine Learning in Customer Service Fraud Detection
- The Human Element: Customer Service Representatives as Fraud Fighters
- The Future of Customer Service Fraud Detection
- Building an Impenetrable Defense with [24]7.ai
In a world that thrives on being digitally connected in both, at the personal and professional fronts, online fraud and data breaches have escalated into a critical business risk. The numbers have been escalating and reveal a growing scale and sophistication of fraud and data breaches.. Studies say that by 2025, the global cost of cybercrime is projected to reach $10.5 trillion, growing at a rate of 15% annually.
The threat landscape has evolved beyond traditional fraud scenarios to the very channels where businesses are executing daily customer experiences such as contact centers, mobile applications, chat platforms, and digital customer service portals. The fraudsters have weaponized technologies originally designed to enhance customer satisfaction, transforming customer service channels into active attack vectors
As fraudulent activities escalate, it’s vital to understand the role of fraud detection; what it is, how it functions, and to explore the solutions to prevent it.

The Customer Service Fraud Paradox
Modern customer service operates on a fundamental paradox. The very technologies that enhance customer experience to flourish also create new vulnerabilities. Today, customer service is juggling security and satisfaction, verification and convenience, while working in a digital minefield where every encounter could be authentic or false.
Fraudsters have been increasingly posing as customer experience representatives in the contemporary scenario. They manipulate customer service channels instead of mirroring genuine empathy and responding to helpfulness with authenticity. By commoditizing customer service engagements, which means they systematically weaponize each customer service channel, which includes phone support, live chat, email support and social media engagement, as an opportunity to monetize trust measures.
The Anatomy of Customer Service Fraud
There are multiple ways of how fraudsters exploit customer-facing service processes, here are some:
- Account Takeover Specialists conduct detailed studies of customer service protocols. They learn precisely what information is used to validate identity and how service representatives respond to distressed customers. They also employ targeted social engineering techniques specifically tailored to exploit these interactions.
- Support Channel Manipulators exploit fragmented multichannel customer service, using information from one channel to authenticate in another. They capitalize on organizational silos, making cross-channel verification challenging.
- Experienced exploiters manipulate customer-centric policies against businesses themselves, exploiting return policies, warranty processes, and goodwill gestures for fraudulent gains.
- Identity Synthesizers create fictional customer personas complete with service histories, complaint patterns, and interaction preferences, making fraudulent requests appear legitimate.

How Fraud Detection Works in Customer Service
Fraud detection operates as a solid shield protecting customers and businesses while maintaining seamless experiences. This process combines behavioral analysis, interaction intelligence, and real-time risk assessment.
Real-Time Interaction Analysis
Modern systems analyze every customer interaction across all channels simultaneously:
- Voice Pattern Recognition recognizes vocal patterns, stress signals, and language indicators suggesting intent to deception. Systems are used to identify the reading of a script, a level of nervousness unrelated to the situation being reported, and identifiable speech patterns associated with deceitful requests.
- Behavioral Consistency Mapping tracks customer interactions across service channels, identifying inconsistencies indicating account takeover or impersonation attempts.
- Request Pattern Analysis examines the nature and timing of service requests, identifying unusual patterns suggesting fraudulent intent.
Intelligent Customer Authentication
Modern fraud detection integrates dynamic authentication considering the entire customer relationship context:
- Historical Interaction Intelligence uses years' worth of records for customer service to create behavioral norms, establishing how customers typically behave when seeking assistance.
- Multi-Channel Correlation aggregates and analyzes all interactions from phone, chat, email or social to create a complete profile of the customer.
- Contextual Risk Scoring evaluates each interaction within a broader account activity context and current threat landscapes.
Machine Learning in Customer Service Fraud Detection
Machine learning has revolutionized fraud detection, transforming reactive security into proactive customer protection:
- Supervised Learning Models analyze historical interactions to identify patterns associated with fraudulent requests, developing sophisticated pattern recognition capabilities surpassing human analytical capacity.
- Unsupervised Learning Algorithms identify previously unknown fraud patterns by detecting anomalies, providing early warning capabilities protecting entire customer bases.
- Natural Language Processing analyzes customer communications across all channels to identify linguistic patterns associated with deceptive intent and social engineering attempts.

The Human Element: Customer Service Representatives as Fraud Fighters
While technology serves as an analytical basis, human representation is the key final component in fraud detection. These individuals act as both customer advocates and security protectors and require some complicated training to understand fraud psychology and know how to identify social engineering actions while continuing to feel empathy.
Fraud mitigation programs enable customer representatives to have reality-check insights for fraud risk, which will allow them to modify their approaches based on the risk level of the interaction. A high-risk interaction will allow them to put heightened verification processes in place, and a low-risk interaction would allow them to proceed with standard service.
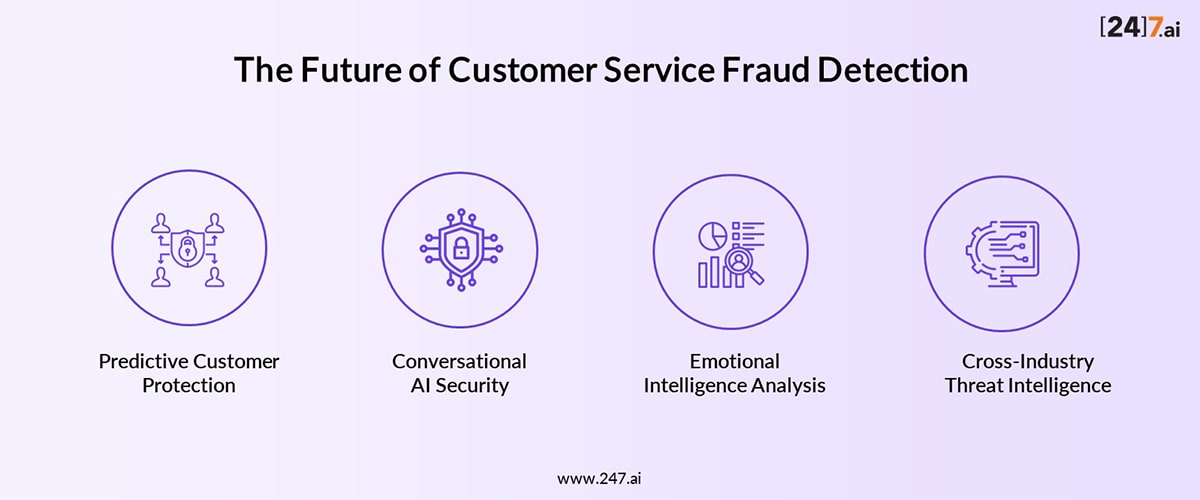
The Future of Customer Service Fraud Detection
The fraud prevention landscape is evolving, moving toward increasingly sophisticated, AI-driven systems that can predict, prevent, and respond to fraud with minimal impact on the customer experience.
- Predictive Customer Protection systems proactively identify customers at elevated risks.
- Conversational AI Security, integrating fraud detection into chatbots and virtual assistants to enable real-time risk assessment.
- Emotional Intelligence Analysis evaluating customer emotional states during interactions
- Cross-Industry Threat Intelligence sharing insights across multiple industries
Building an Impenetrable Defense with [24]7.ai
As we navigate this complex landscape, embracing a zero-trust approach becomes essential. Zero trust operates on the principle of no implicit trust in any user or device. It mandates continuous verification at every access attempt. When combined with zero-fraud principles, organizations can build resilient systems that not only detect but prevent fraud before it occurs.
For organizations seeking comprehensive defense fortification, [24]7.ai’s integrated approach represents the pinnacle of this evolution. The AI-powered omnichannel platform combines zero-trust and zero-fraud frameworks to deliver more than traditional security—it provides complete customer journey protection from initial interaction to long-term relationship building.
By leveraging AI-driven insights, [24]7.ai safeguards the integrity of operations and maintains customer trust. This approach enables organizations to secure their customers and relationships while defending against heightened security risks. It enables organizations to acquire new customers, strengthen existing relationships, and embrace retention, while also utilizing unassailable standards of security.
With increasing cyber threats, standing still equals accepting vulnerability. The future belongs to those organizations that will embrace the security challenges we face and turn them into competitive advantages.
Frequently Asked Questions
Watch for social engineering, unverifiable transactions, urgent requests, or inconsistencies in customer info.
Technology uses ID verification, transaction monitoring, and AI to flag suspicious activity.
Agents verify identities, spot suspicious behavior, and escalate potential fraud cases.
They use layered security and clear communication to reduce fraud while keeping the service smooth.
Train regularly on fraud trends, use simulations, and teach strict authentication and escalation steps.